Data stream management for managed and unmanaged apps for BYO devices.
In both versions of my BYO presentation this fall (JNUC and MacSysAdmin) I use Slack for EMM as an example of how we can use a combination of managed app config (hey, I co-presented a JNUC session on that too!) and MDM restrictions to prevent data sharing between managed and unmanaged sources (or for this example, managed and unmanaged Slack workspaces).
Because the presentations were both so jam-packed (jamf-packed?!) with information I didn't really dig into the specifics of how Slack for EMM and the consumer Slack app can cohabitate on an account-driven user enrolled device and how to put up a theoretical wall between them. Well good news! I have a blog where there is no time limit on things I can talk about.
If you look in the App Store you'll see there are two versions of Slack available; Slack and Slack for EMM. Slack is the consumer flavor of the app and is great for personal or non-organizationally owned workspaces (e.g., the Mac Admins Slack). Slack for EMM is designed to work with Enterprise Grid and has support for a handful of settings that can be enforced via managed app config.
User enrollment has a short list of settings and restrictions available for the managed work container that is created on enrollment. That includes pasteboard restrictions between managed and unmanaged applications. (When reviewing that list, note that if the Supervision column says "no" that means supervision is not required to enforce the setting. BYO devices are unsupervised.)
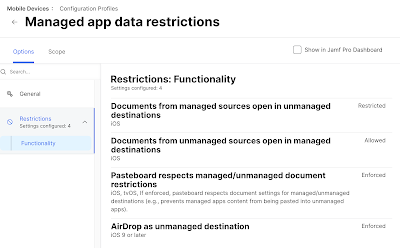
In Jamf Pro, these settings are available in the Restrictions tab for configuration profiles. On the topic of this post—Slack & Slack EMM for BYO mobile devices—the pasteboard restrictions will be applied with a mobile device configuration scoped specifically to devices that are personally-owned.
In the above example the following activities are restricted:
- Documents from managed sources open in unmanaged destinations
- Documents from unmanaged sources open in managed destinations
With those two things set, we can enforce:
- Pasteboard respects managed/unmanaged document restrictions
- AirDrop as unmanaged destination
In a nutshell, these restrictions work together to ensure data from managed apps can only move to other managed apps. Data from unmanaged apps can go to other unmanaged apps or managed apps. And the flow of copy/paste between managed and unmanaged apps respects those documents/destinations restrictions.
When it comes to applying this to Slack and Slack for EMM, the restrictions are not effective enough alone to segment the managed and unmanaged data. After all, what is keeping someone from signing into a non-organizational Slack workspace in the Slack for EMM (managed) app and just keeping copy/paste within that app? This is where managed app config comes in.
With the managed app config options available for Slack for EMM we can enforce via management that only approved workspaces can be used in the managed app.
To ensure that only organizational workspaces can use the Slack for EMM app, set the domain in the WhitelistedDomains key to any work Slack accounts you want to allow (probably just the one, unless you have multiple org units with unique Slack workspaces associated with your Grid). It's also helpful to set the OrgDomain key to streamline the app onboarding/sign-in process for users.
With these settings in place any attempt to sign into a workspace that isn't specified within the managed app config for Slack for EMM will display the following dialog stating that only approved workspaces are allowed.
To ensure that your organizational workspace cannot be accessed in the consumer app (unmanaged) set the ApproveDevice key to SlackAppConfig. This setting enforces that for Enterprise Grid to allow an authentication into an app that the request must come from a managed app with managed app config in place. If not, the login attempt is denied.
With this setting in place an attempt to log into a Slack Grid workspace with SlackAppConfig required will be blocked and display the following dialog stating that only approved devices can log into the workspace.
Ensuring that the Slack workspace is only accessible on a managed application, and that other workspaces cannot be added to that managed app, combines with the pasteboard restriction between managed and unmanaged applications to ensure data from within an organizational Slack workspace stays within that Slack workspace on a BYO mobile device.
You may notice in the available managed app config values that you can disable copy and paste entirely in the Slack for EMM app, but based on limited testing this is a bit maddening. Maybe it's just me, but copying and pasting within the same workspace in the same app (so across channels and messages) seems like something users should be able to do. But I probably don't want users to copy text from messages and paste it into another Slack workspace (or other unmanaged app on a personal device).
Another layer worth considering is the BrowserControl setting, which allows you to route all clicked traffic through a specific managed browser. Combine that with per-app VPN and you can not only have data walled into the managed partition and apps on a personal device, but also across a zero-trust network access connection.
If you read down this far, thanks ✌🏻. I should have slide decks available for both versions of my BYO talk later this month.





Write a comment
Post a Comment