A quick look at a helpful tool for surfacing process activity on a macOS device.
Hey friends! I wanted to throw together a quick post about a great new tool released by the wonderful people over in endpoint security at Jamf.
Jamf Protect Event Analysis is a helper tool used to gain visibility into process activity on a macOS device and is a wonderful companion to the Aftermath tool. From the Github repo:
The jp_event_analysis tool can be used on a Mac endpoint to surface activity that would normally be monitored by Jamf Protect, supporting the Threat Prevention, Analytics (behavioral analysis) and Unified Log filtering features.
Output generated by the tool will indicate the most analyzed activity per feature, providing the required data points about the activity to build Exceptions rules that will cause Jamf Protect to ignore the activity for monitoring and detection.
The script currently supports the following monitors:
• Threat Feed
• Process
• File
• Unified Logging
I won't get too in the weeds here because the Github repo has great information about what the tool is and what it does, so please go check it out.
The repo contains a script that can be run locally adhoc as well as a script designed to run the policy via Self Service. It creates a python 3 environment, installs the requirements, runs the program, and deposits it all into a /tmp directory that opens when the policy completes (and cleans itself up afterwards). The script is easily updated to leverage your own managed_python3 installation if you have that deployed to your fleet.
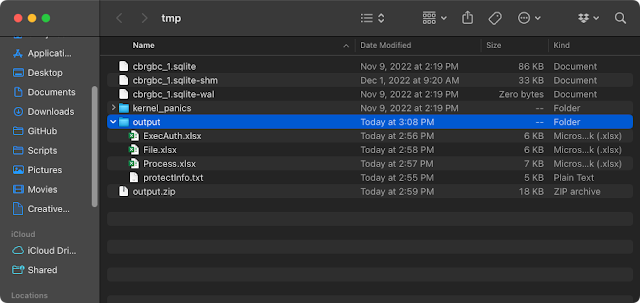 |
| Example output from running the Jamf Protect Event Analysis tool. |
You can find other open source tools made available by Jamf at Jamf's Github space.
☮️❤️☕️

Write a comment
Post a Comment